As we learned in the article Apache NiFi Sensitive Properties: All you need to know about how the sensitive properties are stored and how they are encrypted/decrypted. We came to understand that the encryption key is stored in nifi.properties file. This is not a very good and secure setup to have. In this article, we will learn how to secure the encryption key/password in the properties file.

In order to facilitate this secure setup. We can use the same encrypt-config utility from nifi-toolkit in order to encrypt the sensitive keys in properties file. These values will be stored in encrypted form in the properties file and then decrypted in memory on startup/bootstrap.
1. Apache NiFi Toolkit (encrypt-config)
To encrypt nifi.properties files we will use the command line utility which reads the nifi.properties the file then prompts for a master password and finally using this master password encrypt all the sensitive properties in the file. Encrypt utility can wither overwrite the old file with new or can write a completely new file depending on the parameters passed.
2. Using the toolkit and utility
Let us assume we have the nifi.properties file similar to the screenshot below:
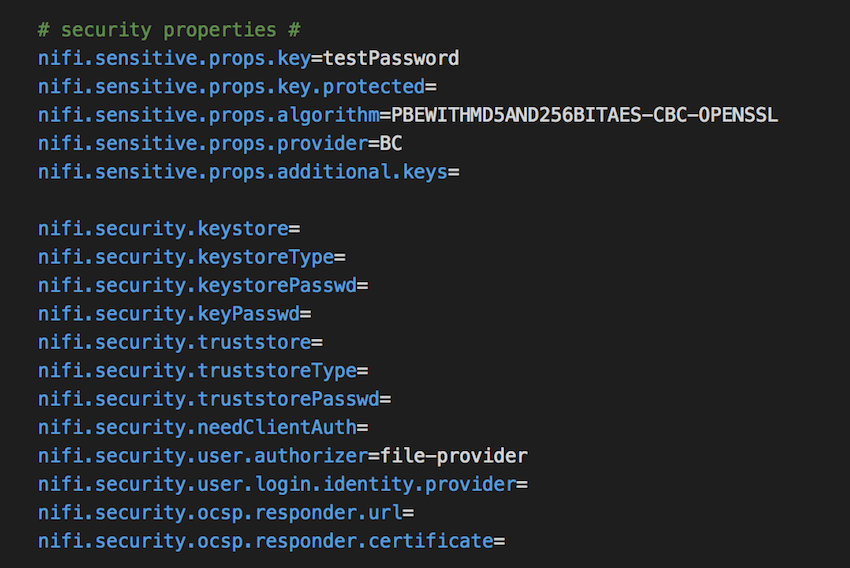
The nifi.sensitive.props.key in the above screenshot have value in plaintext testPassword which is not a very secure way of storing the encryption key in the same file which is used to set all other properties and is accessible by almost everyone.
Execute the following command to encrypt the values in the nifi.properties file:
encrypt-config.sh -b /path/to/bootstrap.conf/file -k 0123456789ABCDEFFEDCBA98765432100123456789ABCDEFFEDCBA9876543210 -n /path/to/nifi.properties/file
The parameters passed are:
-
-b: Path to the
bootstrap.conffile of Apache NiFi - -k: Master encryption key which will be used to encrypt and decrypt the strings
-
-n: Path to
nifi.propertiesfile
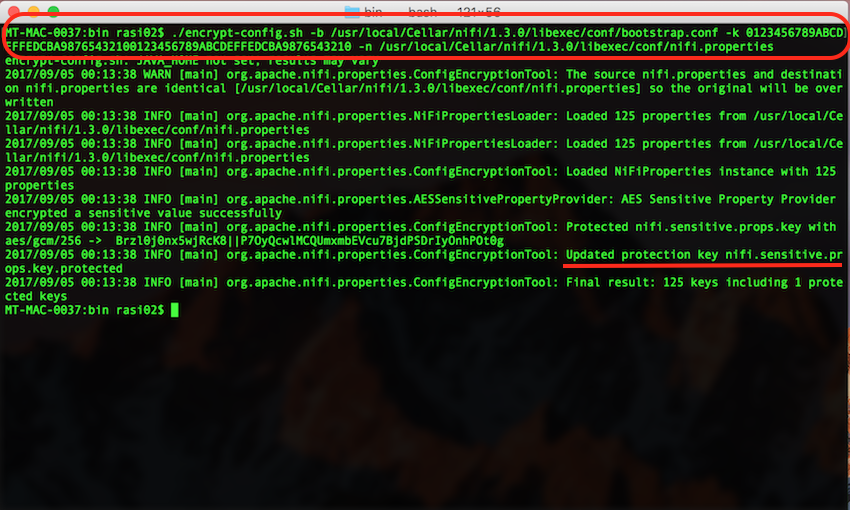
Note the second last entry (underlined in the screenshot above) which indicate that the sensitive properties are successfully encrypted and the properties file is updated successfully.
Upon successful completion, nifi.properties file will be overwritten with encrypted properties as shown in the screenshot below:
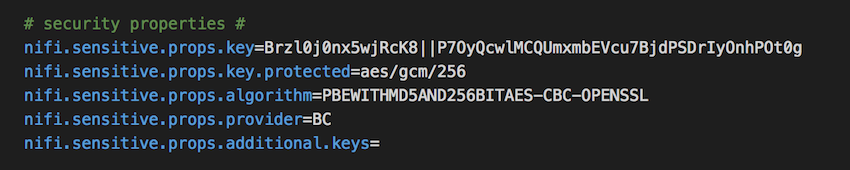
Note: By default, AES/GCM 128/256 bit algorithm is used for encryption, 128 bit will be used if the JCE Unlimited Strength Cryptographic Jurisdiction Policy files are not installed and 256 bit will be used if installed.
In the screenshot above, the value of nifi.sensitive.props.key is encrypted now and the algorithm used is also mentioned as the value of nifi.sensitive.props.key.protected which is aes/gcm/256 in this case as 256 bit algorithm is available on this system.
Besides this, bootstrap.conf file will also be modified and the master key with which all the sensitive properties are encrypted will be stored in the configuration file as a hexadecimal value as shown in the screenshot below.
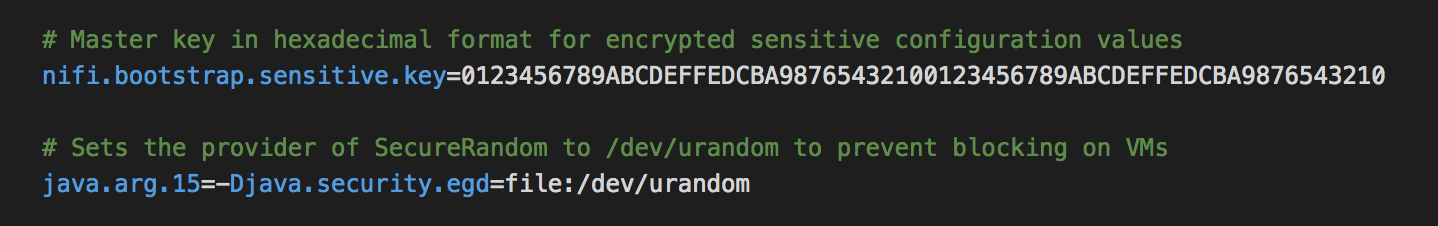
On startup, master key from bootstrap.conf will be used to first decrypt sensitive value from the properties file into memory for later use. The access to the bootstrap.conf file should be restricted to secure the master password even further.
3. Conclusion
In this article, we looked at one more use of the encrypt-config.sh utility provided as a part of nifi-toolkit. We learnt that nifi.properties file store the encryption key used for securing the sensitive properties in the flows is stored as a plaintext value by default which is not much secure. We also learned how to make it more secure by encrypting the keys/password in nifi.propeties file and how the master key is stored and used for decrypting the Nifi properties on startup.
If you found this article useful and would like to read other Apache NiFi related articles, feel free to go through the following related articles:
For more updates from us, don’t forget to subscribe to the newsletter and follow us on social media.
